

Protecting Global Enterprises in a hostile digital landscape. Practical, transparent, and authoritative cybersecurity for the modern era.
Most breaches aren’t “bad luck” — they come from blind spots and slow detection. Close the gaps before attackers find them.
Cybersecurity is the distance between Vulnerability and Visibility. Close the gap today.
Strategic cybersecurity solutions tailored for organizations handling sensitive data. Built for clarity, resilience, and business continuity.
Continuous oversight of your digital perimeter to detect and neutralize threats in real time.
Deep-dive evaluations to identify gaps and measure the maturity of your security controls.
Rapid containment and expert recovery guidance to minimize impact during critical events.
Strategic governance and compliance alignment to ensure executive-level risk visibility.
Deploying and optimizing security tools that align precisely with your business workflows.
Fostering a security-first culture through targeted training and simulation programs.
Building custom, data-private AI agents trained on your organization's specific workflows.
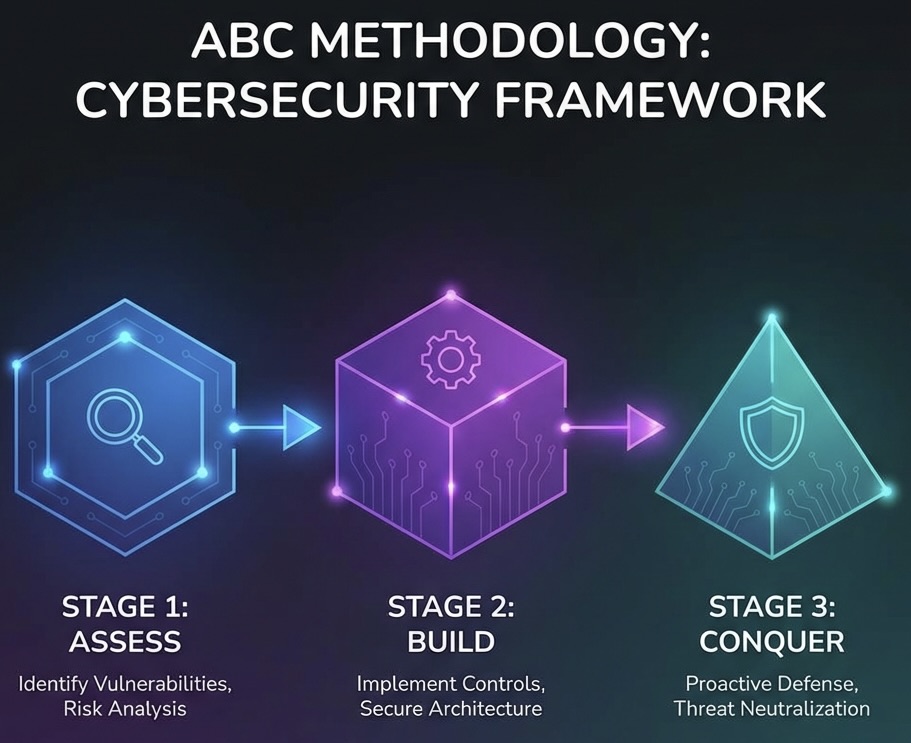
A strategic, multi-stage approach to securing your digital landscape. From initial visibility to always-on protection.
Attack Surface Snapshot
HIQurateOps is an elite cybersecurity firm architected to protect ambitious organizations.
To create a robust digital ecosystem where organizations are no longer easy targets. We bridge the gap between complex threats and operational continuity.
Authoritative & Practical security. No fear-driven tactics. Just raw experience aligned with your business logic.
Quantifiable trends shaping the global cybersecurity landscape.
of breaches involve the human element (Phishing, credential misuse).
Average days required to detect a primary security breach.
of corporate boards now classify cybersecurity as a top strategic priority.
of enterprises globally have experienced a material cyber incident.
Effective security starts with understanding what needs protection, where the risks exist, and how attackers are most likely to exploit them.
Focus on real risks, not noise. Empowering teams with security-first habits and culture to stop threats at the human firewall.
Fix issues before they become incidents. Proactive mapping of vulnerabilities across your entire digital landscape to stay ahead of attackers.
Plans that match your environment and pace. Flexible roadmaps designed to grow with your business needs and risk profile.
Value without enterprise overhead. Maximizing your existing security investment while filling critical gaps with high-impact solutions.
We help organisations build resilience without overwhelming them with tools, jargon, or unnecessary expenses.
Take the first step with a professional Security Baseline Review. Discover your vulnerabilities before attackers do.
Our security experts are ready to assess your operational needs.
End-to-End Encryption Enabled